In today’s world, Internet technology plays a very important role. We have all shifted from the real world to the virtual world. Our jobs, entertainment, daily needs, education, finance, etc., now depend on the virtual world. For all these things, we need a way to interact and fulfill these requirements, and that way is the Internet. But while you are communicating with your family, friends, vendors, service providers, or visiting websites on the World Wide Web, what do you think? How secure are you? Are your messages safe when you communicate with your loved ones on social media? Is your personal information safe when you share it on the Internet? This is where the word “encryption” comes into the picture. Yes, encryption. Encryption is not a new technology. Do you remember, before the Internet, we used letters to communicate, just like the Internet today? At that time, we also used encryption, like protecting our letters inside an envelope to protect our data or personal information. We still use the same technology; only the method is different. Today, the technology is called Encryption Technology or End-to-End Encryption. So, let’s understand end-to-end encryption in detail.
End-to-End Encryption
Introduction: End-to-end encryption is the technology used to prevent information/data from being accessed while being transferred from one source to another, or from one person to another. In end-to-end encryption, only the communicating users can read the messages, not even the social media platforms. For example, while you are texting with your loved ones, only you and your loved one can read the messages; no one else can. In the world of end-to-end encryption technology, there are four main principles at work: 1. Key Generation, 2. Message Encryption, 3. Message Transmission, and 4. Message Decryption. Let’s understand these four key components of end-to-end encryption.
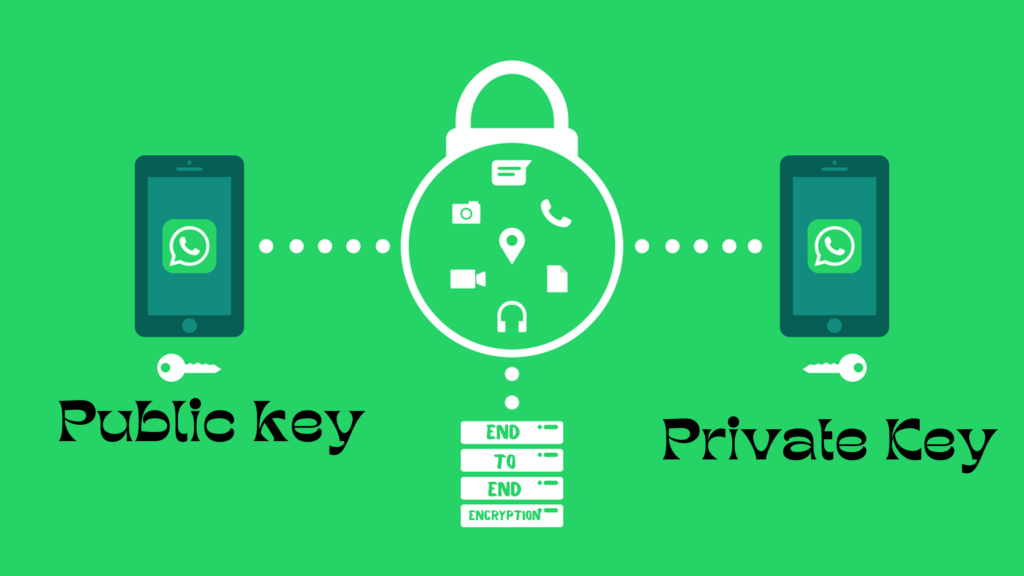
Key Generation
There are two types of encryptions (asymmetric and symmetric). We are discussing asymmetric encryption in this article. The first step of this encryption is key generation. Each user needs to generate a pair of keys to encrypt the message. For example, if user X wants to send “HELLO” to user Y, both users need to generate private and public keys through a responsible “Key Distribution Center.” Generally, RSA (Rivest-Shamir-Adleman), Diffie-Hellman, and Elliptic Curve Cryptography algorithms are used to generate the keys. User Y will share only the public key with user X to send the encrypted “HELLO.” However, the private key remains with user Y. For example, if the public key of user Y is “33,” let’s look at the Message Encryption process.

Message Encryption
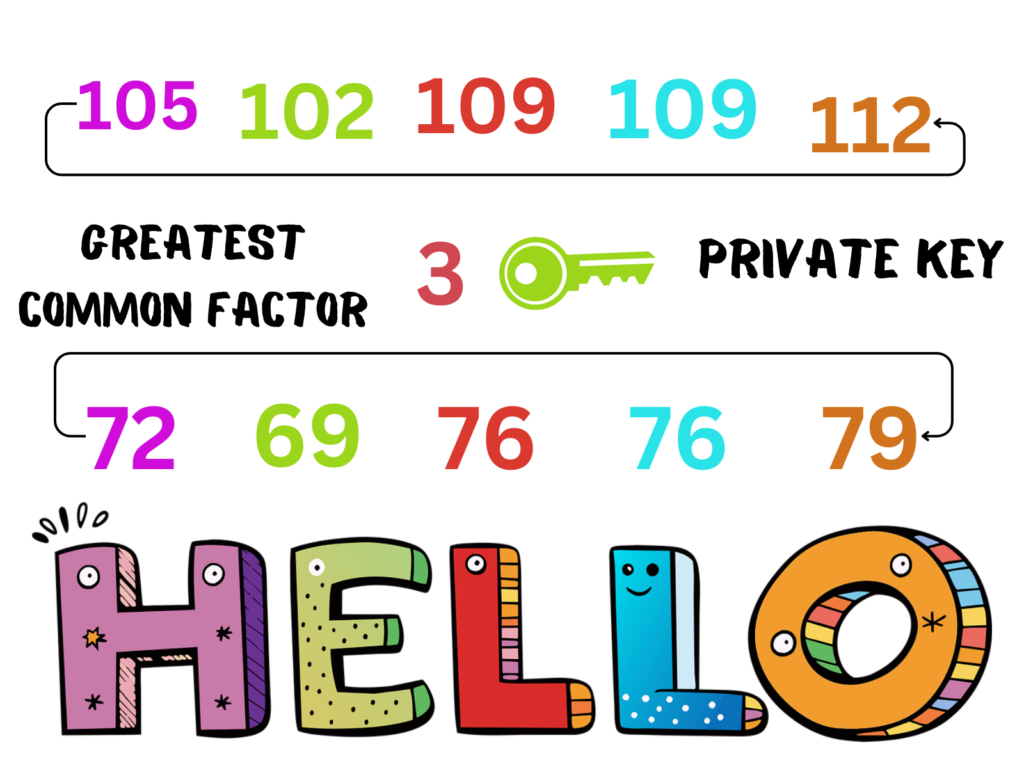
This process involves converting plain text into ciphertext using an algorithm and an encryption key. As we see above, user X wants to send “HELLO” to user Y. Now, encryption technology converts “HELLO” (plain text) to ciphertext (mathematical form) using user Y’s public key (33). This ensures that only user Y can decrypt the message, as only user Y has the private key. Please refer to the image below.

Message Transmission
The encrypted message is transmitted over the network to user Y. Even if a hacker tries to read the message/information, they cannot read it because they do not have the private key to decrypt it. The information is encrypted by a very secure algorithm. As discussed earlier, the factorization of very long prime numbers is used in the algorithm. Hence, it is very difficult and time-consuming to generate the duplicate private key. As hackers don’t know which prime numbers are being used, they need to check all possible prime numbers. Meanwhile, the information is already delivered to its destination.
Message Decryption
Now, the last process comes into play. User Y receives the message in the form of ciphertext. User Y then decrypts the ciphertext message into plain text (HELLO) using the private key(3). See the example image.
Conclusion
End-to-End encryption ensures maximum privacy and security by limiting message reading to only the conversing users and encrypting data. Since only the receiver user owns the matching private key, users confident they are speaking with the correct individual. The core of End-to-Encryption security is the key generation process. Asymmetric encryption is frequently used, and it requires using mathematical procedures like RSA or ECC to generate the public and private keys. Because it is impossible to factor the product of two huge prime numbers, RSA is secure. Private keys should be stored safely and are frequently secured with passwords or hardware security modules (HSMs). Even when the data is encrypted, third parties may still be able to see metadata about who is talking to whom and when.


